
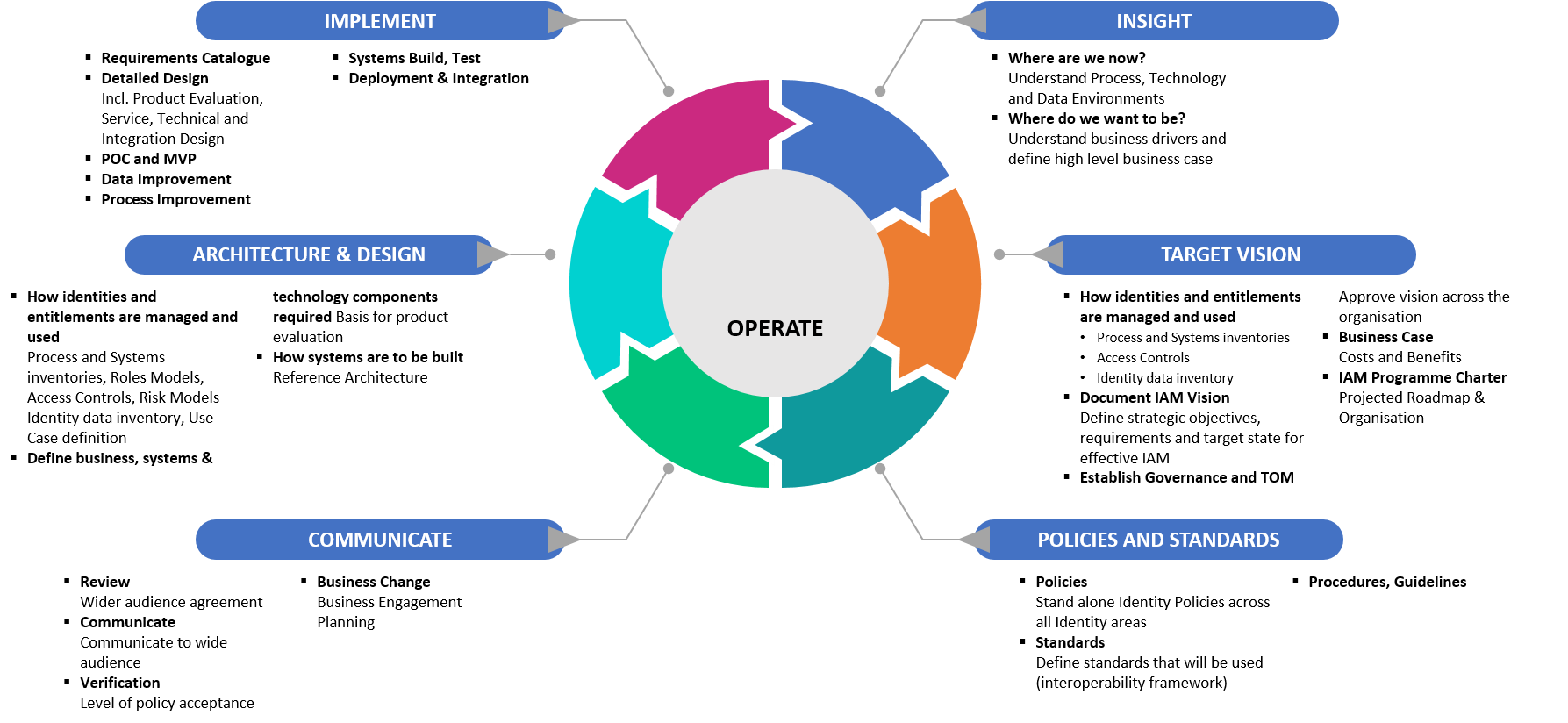
What Business Challenges are driving the
need for effective
IAM?
Risk and Compliance
- Security breaches are occurring at an alarming rate. In modern extended enterprises, identity and context are the only points of control that now remain.
- Digital Identity is the main point of control that organizations still have over information in a world where users own the clients, bring their own identities, and outsourcers own the servers.
Cost
- Reduce costs associated with the governance and management of user access across the enterprise, including the costs of running flexible underpinning IAM services.
- Unlike many other areas of cybersecurity, IAM can provide positive ROI benefits in terms of process improvement. But IAM projects can be costly, difficult to control and frequently fail to deliver expected benefits.
Business Enablement
- Security breaches are occurring at an alarming rate. In modern extended enterprises, identity and context are the only points of control that now remain.
- Digital Identity is the main point of control that organizations still have over information in a world where users own the clients, bring their own identities, and outsourcers own the servers.
Digital Transformation is underpinned by IAM

Business Focused, Agile & Iterative
IAM Professional Services
Identity Governance and Administration (IGA)
- Identity Life-Cycle Management
- Automated Provisioning
- Password Management
- Self-Service/Delegation
- Fine Grained Entitlement Management
- Access Certification
- Role Management & SoD (Separation of Duty)

Identity Storage
- Integrate with Identity Management system
- Leverage Existing Corporate Directory for Windows SSO
- AD/Azure AD and LDAP as User Store.
- Configured Virtual Directory server for Authenticating.
- External and 3rd parties users.

Privileged Access Management (PAM)
- Privilege Session Management
- Vault for privileged users
- Role Based Provisioning of Privileged accounts
- Audit and Reporting – Sessions

Authentication
- Adaptive Authentication.
- Multi-Factor Authentication (MFA).
- Managed Authentication.
- Location Based Risk Profiling.
- Biometrics

Consumer IAM (CIAM)
- Customer Registration
- Consent Management
- Consumer APIs
- Consumer SSO
- Identity Intelligence

Access Management
- Web Access management/OS Access Control.
- Enterprise Single Sign On
- Web Single Sign On.
- Federation Services.
- Role Based Access Management.